Over 50 percent of businesses in Germany have been targeted by a cyber attack. The number of attacks in the digital space has significantly increased in recent years, causing billions of euros in damage each year. With the advent of digitalization, the number of attacks is likely to continue to rise. However, businesses are not defenseless against these cyber risks.
What are Cyber Risks?
Cyber risks are those risks that arise in the digital space. In the digitally connected world, there are various types of risks, a large part of which are criminal activities.
What does digitalization mean for businesses? We inform you about this in our blog post.
- Cyber risks are deviations from the target plan that occur in cyberspace.
- Criminal attacks, Force Majeure, as well as technical and human failures are the main types of cyber risks.
- With cyber insurance, companies and freelancers can protect themselves from the economic consequences of a cyber attack.
To process large amounts of data, companies need an all-in-one software solution. You can learn about the advantages of a Big Data Analytics platform on on of our expertise site.
KEY POINTS
- Over 50% of businesses in Germany have already been targeted by a cyber-attack, with damages in the billions and an increasing trend in the digital age.
- Cyber risks, ranging from criminal activities to technical and human failures, can paralyze the entire IT infrastructure and lead to significant revenue losses.
- Companies can minimize cyber risks through secured IT infrastructure, awareness, and cyber insurance, to protect themselves from the economic consequences of cyber attacks.
Reasons for the Increase in Cyber Risks
- Increasing electronic networking
- Continuously growing data volume
- Industry 4.0
- Internet of Things
Cybersecurity has gained importance in the course of digitalization. What do the terms Web1, Web2, and Web3 mean? You can find out in our blog. Interested in a guide to Generative AI? You can also find this information in our blog.
Cyber Risks are Diverse
This term encompasses various risks that lead to deviations from the target plan. Cyber risks can be caused by deliberate and targeted attacks on data or IT systems. It’s also possible for attackers to use the internet and social media for targeted campaigns at the expense of individual companies. Even unintended attacks from cyberspace can lead to the failure of the entire IT infrastructure and revenue losses. A USB stick with sensitive data forgotten on a train can also have serious consequences. You can find more information about data protection on the website of the Federal Commissioner for Data Protection and Freedom of Information.
Who is Affected by Cyber Risks?
Any business that uses digital systems for communication or data processing is affected by cyber risks. Therefore, companies in all industries are fundamentally at risk. Manufacturing companies and service providers (e.g., banks and insurance companies) are equally affected.
Find qualified Cyber-Security Specialists.
Company Size and Cyber Risks
Although large companies are disproportionately often targeted by cyber attacks, cyber risks particularly affect small and medium–sized businesses. Unlike large corporations, these usually do not have their own IT department and have not yet implemented comprehensive security measures. Often, they lack the time and resources to fully protect their IT infrastructure. Individual entrepreneurs and freelancers are also affected by cyber risks. A successful cyber attack can cause significant damage. Particularly for medium-sized businesses and small entrepreneurs, the consequences of data loss, business interruption, or operational errors can be existential.
IT Outsourcing and Data Analyst
Possible Consequences of Neglecting Cyber Risks
- Breach of data confidentiality
- Breach of system or data integrity
- Impairment of the IT system’s functionality
- Production interruption or supply chain disruption
- Defamation campaign or boycott call against a company
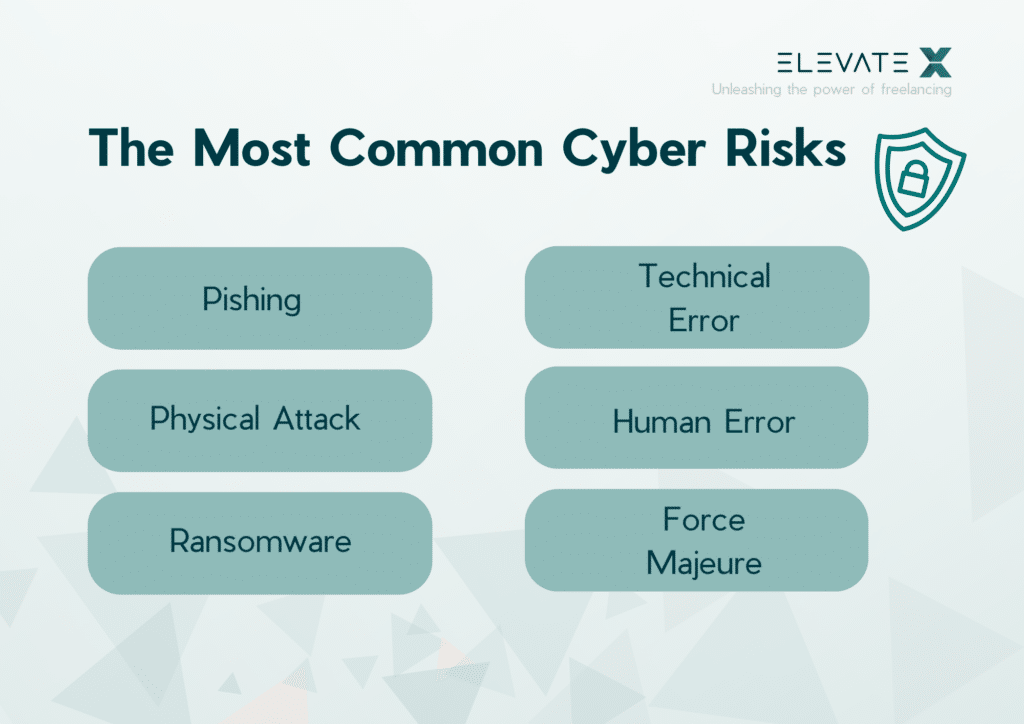
The Most Common Cyber Risks
1. Phishing (espionage of trade secrets and data protection violations)
Phishing involves sending compromised emails to unsuspecting individuals who then open the risky attachment. Through phishing, attackers can steal login data and thus gain access to entire corporate networks. In this way, the hacker can spy on trade secrets. Almost everyone knows what a hacker is. But not everyone is familiar with the Hacker School, which helps young people gain programming experience and insights into IT professions. You can find more information in our blog.
2. Physical Attack
The physical attack is similar in its objective to a hacker attack. The difference lies in the fact that the attacker does not use tools but gains access to the IT system by breaking into the company building. Sometimes it’s an employee who steals confidential data and misuses the existing access to the information.
3. Ransomware
Using ransomware, hackers encrypt sensitive data and ensure that it can only be decrypted after a ransom is paid. In the worst case, companies pay the ransom but still do not regain access to their data. Extortion cases involving crypto-trojans make up a large part of the cyber risks for small and medium–sized companies. More information on ransomware attacks can be found on the website of the Federal Office for Information Security.
4. Technical Failure (Hardware or Software)
A hardware defect or software error can lead to data loss. Possible scenarios include overheating of the computer, a short circuit in the system technology, and head crashes of hard drives. A functioning IT is one of the key success factors in business value creation. External IT services are an attractive option for many companies.
5. Human Error
Human error includes the loss of data carriers and the accidental publication of sensitive data. Human error, in combination with phishing, can lead to significant damage. A single careless click is enough for a cyber attacker to gain access to sensitive data. Cyber risks also affect the home office.
6. Force Majeure
Force Majeure refers to causes that are neither criminal in nature nor due to human or technical failure. These include, for example, severe weather and power outages.
Consequential Costs of Cyber Attacks
Not only does repairing damaged systems cost a lot of money. Secondary costs (e.g., contractual penalties, fines, lawyer and court costs) should not be underestimated. More information about fines for violations of the General Data Protection Regulation (GDPR) can be found on this portal.
Protection Against Cyber Risks
With a secured IT infrastructure, you can minimize cyber risks in advance. Sensitivity to cyber risks in companies is also an important factor in prevention. Young professionals are already interested in protection against hacker attacks and internet crime. Find out about opportunities to actively promote IT talent in our blog!
Specialists for Cyber Security
Numerous companies utilize the expertise of specialists who know the typical vulnerabilities in IT infrastructure and train the staff accordingly. What can freelancers contribute in this context? You can find valuable information on our site. As an agile IT community, ElevateX is happy to help you find a full-stack developer.
Protection Through Cyber Insurance
Cyber insurance offers effective protection for companies and their staff against financial losses resulting from cyber attacks. Usual business insurances and professional indemnity insurances cover cyber risks only insufficiently. Companies that take out cyber insurance protect themselves from the economic consequences of criminal attacks and also benefit from emergency services.
Information From Bürger-CERT
The Federal Office for Information Security informs the public about risks in the digital space, current warnings, and specific security situations. More information can be found on the website of the Federal Office for Information Security.
Conclusion
Cyber risks are increasing. Among the real dangers are both covert cyber attacks, such as phishing, and the introduction of malware, such as ransomware. Targets of criminal cyber attacks are the disruption of availability, integrity, and confidentiality of IT systems in the respective companies. Weather-related events, power outages, hardware failures, software errors, and human error are also serious threats. The costs in the event of damage are considerable. Strengthening cyber security is therefore a crucial factor for the economic success of the company. This commitment can give the business significant competitive advantages.
This term encompasses various risks, a significant category being targeted attacks on data or IT systems through the misuse of information and communication technology.
Criminal attacks, power outages, technical and human failures are among the dangerous cyber risks for companies.
By securing the IT infrastructure and having cyber insurance, companies, businesses, and freelancers can minimize or completely avoid the consequential costs in the event of an attack. Thus, they are protected from economic damages.